Press release
Positive Technologies: Attackers Customize Malware to Conduct Attacks on Virtual Infrastructure
Positive Technologies today unveiled its Cybersecurity Threatscape Q1 2021 research report, which finds cyber incidents continue to rise, ransomware accounts for nearly two-thirds of all malware attacks, and more cybercriminals are customizing malware for attacks on virtual infrastructure.The quarterly report shares information on relevant global cybersecurity threats, with data based on Positive Technologies expertise and investigations, as well as data from authoritative sources, produced for companies and citizens concerned with the state of information security. It looks at cyberattack key motives and methods, and highlights changing cyberthreat landscape trends.
According to the research, the number of attacks increased by 17% compared to Q1 2020, with 77% being targeted attacks, and incidents with individuals accounting for 12% of the total. Cybercriminals attacked government institutions, industrial companies, scientific organizations, and educational institutions the most. Their main targets are personal data and credentials, and attacks on organizations are also aimed at stealing commercial secrets.
The research shows that ransomware remains the most common malware. Its share, among other malware used in attacks on organizations, increased by seven percentage points compared to Q4 2020, now accounting for 63% of all malware. The report also finds Q1 saw several new pieces of ransomware emerge -- for example, Cring, Humble, and Vovalex. And WannaCry is reported to be running rampant again, which made a name for itself in 2017.
Positive Technologies analyst, Yana Yurakova said: “Malware developers keep looking for new ways to bypass security tools. They’re using unpopular programming languages to fly under the radar, as in the case of BazarBackdoor (a remote access tool), which was rewritten in Nim. The operators of Vovalex and RobbinHood (ransomware programs) chose uncommon languages such as D and Golang, respectively, from the get-go. Some attackers upgrade their tools with features that erase traces of malicious activity.”
The report also finds the ransom amounts demanded by ransomware operators continue to grow, and due to the fact that some companies refuse to pay, attackers come up with new extortion tactics – for example, they threaten to report the attack and data theft to a victim’s customers, expecting that the customers will persuade the company to pay a ransom to prevent the disclosure of their personal data.
More and more cybercriminals are developing malware to conduct attacks on virtualization environments, and some are aggressively trying to exploit vulnerabilities already found in software for deploying virtual infrastructure. The experts link this primarily to the global process of moving corporate IT infrastructure into a virtual environment.
Dmitry Serebryannikov, Director of Security Analysis, Positive Technologies, said: “Attackers carefully monitor information about new vulnerabilities and try to find a use for these in their attacks as soon as possible. In early 2021, Positive Technologies researchers helped eliminate several critical vulnerabilities in VMware products, including CVE-2021-21972 in vCenter Server, which allowed remote code execution. After the vendor's security updates appeared in early February and the bulletin was published, Bad Packets researchers discovered multiple network scans conducted to find vulnerable hosts. We strongly recommend installing the security updates as soon as possible.”
The research also finds the number of attacks targeting IT companies remains consistently high for the second quarter in a row. In 15% of cases during Q1 2021, hackers targeted IT companies to conduct an attack on their customers or to steal customer data. At the beginning of 2021, there were still reports in the media about new victims of the attack on SolarWinds.
Access a full copy of the report here: https://www.ptsecurity.com/ww-en/analytics/cybersecurity-threatscape-2021-q1/.
MEDIA CONTACT:
Paula Dunne
CONTOS DUNNE COMMUNICATIONS
+1-408-893-8750 (m)
+1-408-776-1400 (o)
paula@contosdunne.com
Positive Technologies:
8 Preobrazhenskaya Square, Moscow, 107061
+7 495 744 01 44
About Positive Technologies
Positive Technologies is a leading global provider of enterprise security solutions for vulnerability and compliance management, incident and threat analysis, and application protection. Commitment to clients and research has earned Positive Technologies a reputation as one of the foremost authorities on Industrial Control System, Banking, Telecom, Web Application, and ERP security, supported by recognition from the analyst community.
ptsecurity.com, facebook.com/PositiveTechnologies, facebook.com/PHDays.
This release was published on openPR.
Permanent link to this press release:
Copy
Please set a link in the press area of your homepage to this press release on openPR. openPR disclaims liability for any content contained in this release.
You can edit or delete your press release Positive Technologies: Attackers Customize Malware to Conduct Attacks on Virtual Infrastructure here
News-ID: 2330704 • Views: …
More Releases from Positive Technologies
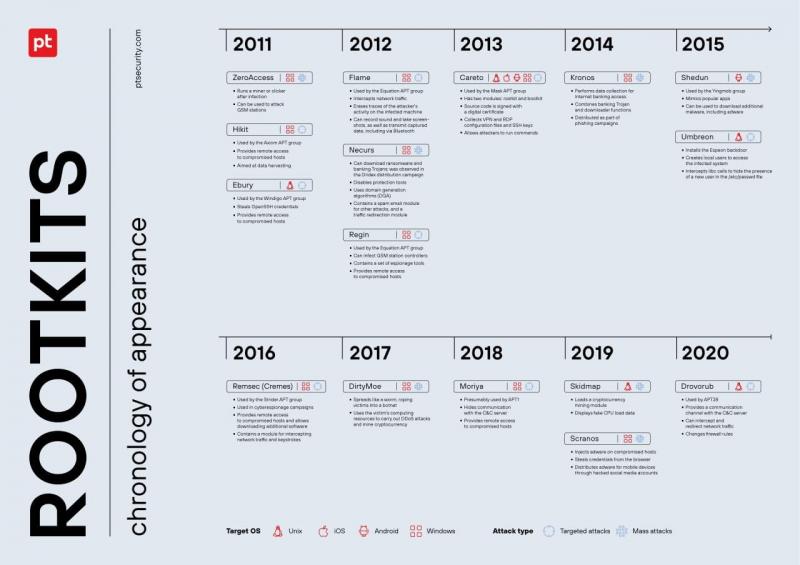
Positive Technologies Report Examines the Evolution and Current Threat of Rootki …
Difficult and Costly to Create, These Malicious Programs That Hide the Presence of Malware Target Governments and Research Institutes, and Are Here to Stay
November 3, 2021 – In a new report, Positive Technologies analyzes this past decade's most infamous families of rootkits—programs that hide the presence of malicious software or traces of intrusion in victim systems. The study finds that the majority of rootkits are used by APT…

New Report from Positive Technologies Finds Ransomware Attacks Have Reached ‘S …
September 22, 2021 – Ransomware attacks have reached ‘stratospheric’ levels, now accounting for 69% of all attacks involving malware. That is among the most disturbing finding in “Cybersecurity Threatscape: Q2 2021,” the latest report from security specialist Positive Technologies. The research also reveals that the volume of attacks on governmental institutions in particular soared from 12% in Q1 2021 to 20% in Q2. And the company’s Expert Security Center (PT…
More Releases for Yana
myPOS launches the elegant, powerful myPOS Slim device on the EU market
With an increasing number of businesses using barcode scanners to keep their inventory in order, European fintech myPOS has recognised this need and is tailor-making its offering to merchants in the European market with the brand-new addition of a new payment terminal. myPOS Slim is the ideal payment companion for a wide range of businesses including logistics and delivery companies/couriers as well as those in the retail and food &…
NAKIVO automatisiert VM Disaster Recovery für VMware, Hyper-V und AWS in der ko …
NAKIVO automatisiert VM Disaster Recovery für VMware, Hyper-V und AWS in der kommenden Version v7.4
NAKIVO Backup & Replication v7.4, geplant für die Veröffentlichung im 1.Halbjahr 2018, bietet eine Vielzahl neuer Features, um die Leistungsfähigkeit von VM-Datensicherungen zu erhöhen, die Zuverlässigkeit zu verbessern und die Wiederherstellung in Cloud-Umgebungen zu verbessern.
NAKIVO, Inc., ein schnell wachsendes Virtualisierungs- und Cloud-Backup-Softwareunternehmen, gab heute die bevorstehende NAKIVO Backup & Replication v7.4 bekannt. Die Anmeldung für die…
TULA recognized by CIO Applications magazine as "Top 25 GRC Technology Providers …
In the wake of the growing need of GRC technology solutions across enterprises globally, CIO Applications has compiled a list of “Top 25 Governance, Risk, and Compliance Technology Providers 2017.” The compilation is a result of extensive research of GRC technology providers worldwide, conducted by the editorial team.
DDi caters to Clinical, Regulatory, Safety, and Enterprise domains with its innovative technology products and automation solutions for Life Science organizations.
DDi developed…
NAKIVO startet v7.2 Beta mit ASUSTOR NAS Unterstützung und neuen Funktionalitä …
NAKIVO Backup & Replication v7.2 Beta kann auf ASUSTOR NAS installiert werden und bietet Transaktionsprotokolltrunkierung (Abschneiden des Protokolls) und Instant Object Recovery für Microsoft SQL Server an.
NAKIVO Inc., eines der am schnellsten wachsenden Virtualisierungs- und Cloud-Backup-Software-Unternehmen, gab heute bekannt, dass es ein offenes Beta-Programm für NAKIVO Backup & Replication v7.2 gestartet hat. Die v7.2 Beta steht zum Herunterladen zur Verfügung und hat neue Funktionalitäten, um die VM-Sicherung und Wiederherstellung zu…
Mit NAKIVO vermindert Firma Mondialpol Verwaltungszeit von VM-Backup um 20 %
Mondialpol Service Group, ein italienischer Anbieter der Dienstleistungen von Objektschutz, verwendet NAKIVO Backup & Replication, um ihre VMware-Umgebung zu schützen, und reduziert Verwaltungszeit von VM-Backup um 20 %.
NAKIVO Inc., ein schnell wachsendes Softwareunternehmen für Schutz der virtualisierten und Cloud-Umgebungen, hat heute bekannt gegeben, dass Mondialpol Service Group, ein italienischer Anbieter der Dienstleistungen von Objektschutz, hat NAKIVO Backup & Replication ausgewählt, um ihre VMware-Umgebung zu schützen.
Mondialpol Service Group…
New Publication: Wandering Workers
"Wandering Workers – Mores, Behavior, Way of Life, and Political Status of Domestic Russian Labor Migrants" by Juri Plusnin, Yana Zausaeva, Natalia Zhidkevich, and Artemy Pozanenko, offers a fresh perspective on the issue of contemporary migratory labor.
The russian term otkhodnichestvo stands for the temporary departure of inhabitants from small towns and villages for short-term jobs in the major cities of Russia. Based on numerous interviews with otkhodniks and local experts,…
