Press release
Log4j threats: Everything you should know about
Log4J is the worst vulnerability in the last 10 years and hence it is not a surprise.You must have heard a lot about the Log4j vulnerability till now!
Presently, it is also the mostly searched technical keyword on Google when it comes to security.
Let me explain the problem in simple words.
- It is a threat detected in the Log4j library of Java.
- Nov 24th, 2021: First, Alibaba Cloud Security team disclosed this vulnerability to Apache.
- Dec 9th, 2021: The vulnerability formally designated CVE-2021-44228 was revealed on Twitter.
- December 10: UK NCSC warned UK organizations about Log4j.
- December 11: CISA director remarked on “urgent challenge to network defenders”
- December 14: Second Log4j threat with denial-of-service threat was identified and new patch was released as mitigation.
- December 17: Third Log4j vulnerability was detected and a new fix was released.
- December 20: Log4j was exploited by the hackers to install Dridex and Meterpreter.
What is Log4j?
Apache Log4j is a Java-based logging library originally written by Ceki Gülcü. It is a project by Apache Software Foundation and a part of the Apache Logging Services.
How Log4j can affect you?
Read our blog to understand how to mitigate Log4j vulnerabilities. https://aaic.cc/mmrk
The Log4j vulnerability can affect a prevalent component that is not popular or not known by everyone. The new name of this bug is Log4jshell.
More than 13 billion devices around the world run on Java and Log4jshell is affecting all the devices that are using a specific version of Log4j.
Being a high-level object-oriented language, Java is widely used. For example, if you are playing Minecraft, you are using Java, if you are using android phones, you are using Java, and if you are using smart TVs, you are using Java.
Not all Log4j versions are vulnerable!
Only the devices running Apache Log4j with versions from 2.0 to 2.14.1 are vulnerable to this risk. As per NCSC, the affected version i.e. Log4j2 is contained in Struts2, Apache Solr, Druid, Swift, and Flink frameworks.
The logging library of Log4j comprises various logging information like date, time, user name, and many more from the chatroom, web server logs, etc.
But hackers are attacking this library with remote code execution (RCE). This means the hackers are trying to fetch the value in a form from a remote site.
Generally, they point a URL to a Java class, fetch the code and insert it into a memory. The code runs without getting checked for legitimacy and Voila ! You are hacked.
Real things we have done for our customer to mitigate Log4j threats:-
Two of our prime customers got affected with Log4j vulnerabilities. But thanks to our prompt IT security team. For one of the customers, we have upgraded the Log4j library version.
On the other hand, our certified team of AWS experts configured AWS Web Application Firewall (WAF) in their cloud environment.
Our prompt and strategic action saved our customer’s business continuity.
As a leading AWS consulting partner, we are happy to share that Amazon OpenSearch Service released a service software update – R20211203-P2. It comprises an updated version of Log4j2 for all regions. And we are helping all of our customers in updating their OpenSearch clusters to this release.
To know more talk to our AWS security experts@ https://aaic.cc/1ax4
Sky Loft, Creaticity Mall, Off, Airport Rd, opposite Golf Course, Shastrinagar, Yerawada, Pune, Maharashtra - 411006
We are automation experts, with an AWS-certified team comprising 60% of our workforce. We assist you in applying intelligence to cloud and DevOps, as our name suggests.
Our AWS certified experts create high-performing cloud apps by utilising intelligent components and smart integrations to accelerate your digital transformation journey.
This release was published on openPR.
Permanent link to this press release:
Copy
Please set a link in the press area of your homepage to this press release on openPR. openPR disclaims liability for any content contained in this release.
You can edit or delete your press release Log4j threats: Everything you should know about here
News-ID: 2546205 • Views: …
More Releases from Applied AI Consulting

Applied AI Consulting Got a Bigger Place for its Growing Team Size
Moving to a new bigger and nicer place is one of the most exciting experiences companies can have. It's a clear signal to their growing team size and clients list. And for Applied AI Consulting, it's special for various other reasons as well.
"During the covid, while companies were laying off, we continuously hired new talents and grew tremendously. From 30+ employees to now 100+ employees, we build a pool…

Applied AI Consulting Earned ISO 27001:2022 Certification
ISO:27001 certification was acquired by Applied AI Consulting, a prominent Cloud and AI automation service. This certification was earned after a lengthy audit.
One of the most well recognised and acknowledged information security standards in the world is ISO 27001. AAIC has further established itself as one of the most secure service providers on the market by acquiring this certification. It's a result of our comprehensive security procedures and policies that…
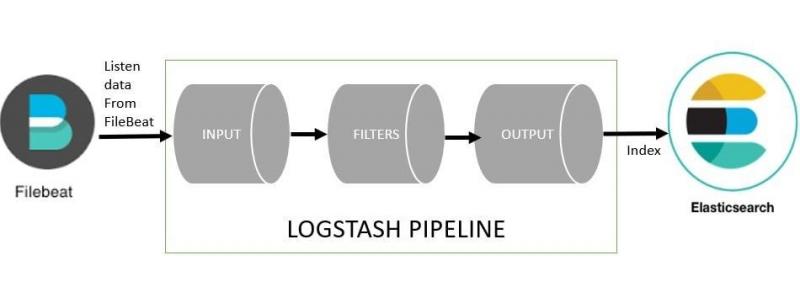
What is Filebeat and why it is imperative?
The beats are open-source and lightweight data shippers. You can install these as agents on your servers to dispatch operational data to Elasticsearch. You can send data directly via beats to Elasticsearch or via Logstash. Here (in Logstash) you can further process and develop the data.
Filebeat creates a low memory footprint to forward and centralize logs and files and you don't need to use SSH especially when you have…
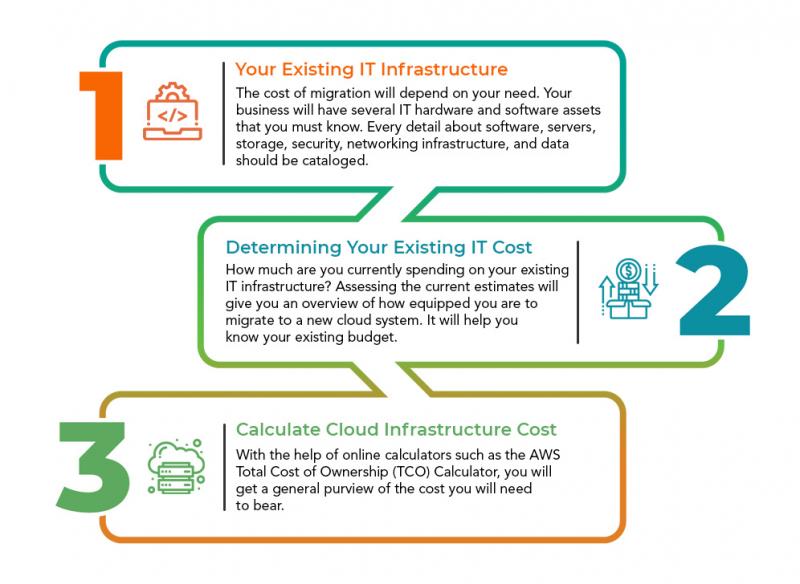
The Ultimate Cost of AWS Migration Checklist
Migrating to the cloud is the need of the hour for any business. It is a well-established fact that the AWS Cloud environment is easy to use, offers flexibility to businesses, is scalable, secure, and reliable.
But before jumping ship, you would want to know the cost of cloud migration - specifically to Amazon Web Services (AWS).
Cloud systems offer hordes of cost benefits, which is what makes them so attractive.
1.…
More Releases for Log4j
Aviation & Defense Cyber Security Market Thriving at a Tremendous Growth | Thale …
Global Aviation & Defense Cyber Security Market Size Study Size, by Components (Solution, Service), by Deployment (On- Cloud, On-Premise) and Regional Forecasts 2022-2028, Covid 19 Outbreak Impact research report added by Report Ocean, is an in-depth analysis of market characteristics, size and growth, segmentation, regional and country breakdowns, competitive landscape, market shares, trends and strategies for this market. It traces the market's historic and forecast market growth by geography. It…
PDF Library introduces consolidated logging
London, England, 08 July 2009, - Big Faceless Organization (BFO), provider of high quality Java software components, have enhanced the PDF library by introducing consolidated logging. Version 2.11.6 of the Big Faceless PDF Library also includes a thread clean up.
Previously log messages were written to System.err. If problems were encountered PDFs could throw a large number of messages, and although these could always be turned off, there was no way…
